What is a reverse proxy: how do they work, who needs them, and why
Proxy services are used for a variety of reasons by individuals and companies alike. For companies running websites or web applications, a reverse proxy is the most commonly used type, and this is largely due to the fact that they offer many benefits, especially when it comes to securing and speeding up the website. A reverse proxy is a gateway, positioned between the client (the browser of a user) and the backend server of the web application or website.
In this blog post, we’re going to discuss everything there is to learn about reverse proxy, with a mention of how they function, the most important applications, the benefits they offer, and the issues most people planning to deploy them should be aware of. But before we proceed with that, let’s have a brief overview of the basics of reverse proxies.
Article’s Key Takeways
- A reverse proxy is a gateway between users and backend servers, handling requests, distributing traffic, and adding layers of security without exposing server details.
- Unlike forward proxies, which primarily serve users seeking anonymity or filtered access, reverse proxies are designed to protect and optimize websites by managing SSL encryption, load balancing, caching, and blocking malicious traffic.
- They play a critical role in safeguarding businesses against DDoS attacks, filtering threats, and ensuring data privacy while also improving speed and scalability for high-demand applications.
- Common use cases include securing unmanaged devices, protecting sensitive data, enabling consistent load distribution, and enhancing performance for global platforms like streaming services.
- However, challenges such as complex setup, added latency, misconfiguration risks, and potential single points of failure mean organizations must implement careful configuration, redundancy, and monitoring for effective deployment.
- ProxyWing offers affordable and reliable reverse proxy IPs for its customers.
Understanding the Concept of Reverse Proxy Server
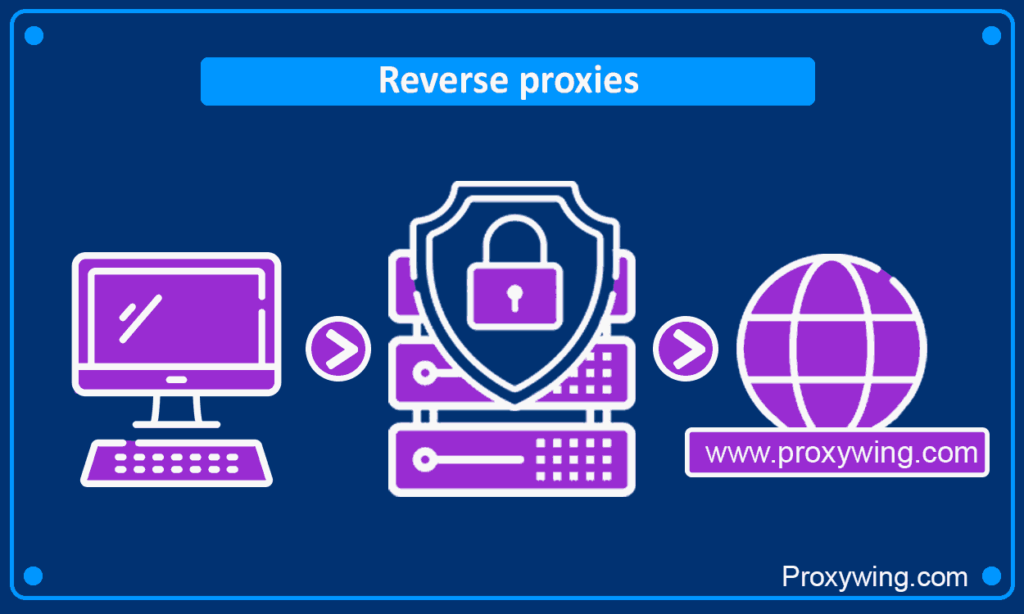
A reverse proxy is a server that exists between a web server and clients, intercepting connection requests from clients and sending them to the intended backend server. Whether the web application is hosted using a single or multiple backend web servers, the proxy can be used to route incoming traffic.
It can carry out operations like load balancing, caching, and security filtering, thus improving web application security and website performance. For instance, when a client requests to access a web site, the reverse proxy can decide which server to forward the request to depending on its type and configuration of the request initiated.
How is a reverse proxy different from other types?
The most common types are forward and reverse proxies. The two differ mainly in their purpose and the audience they cater to. Let us see how different they are.
Main Differences Between Forward and Reverse Proxies
Forward Proxy
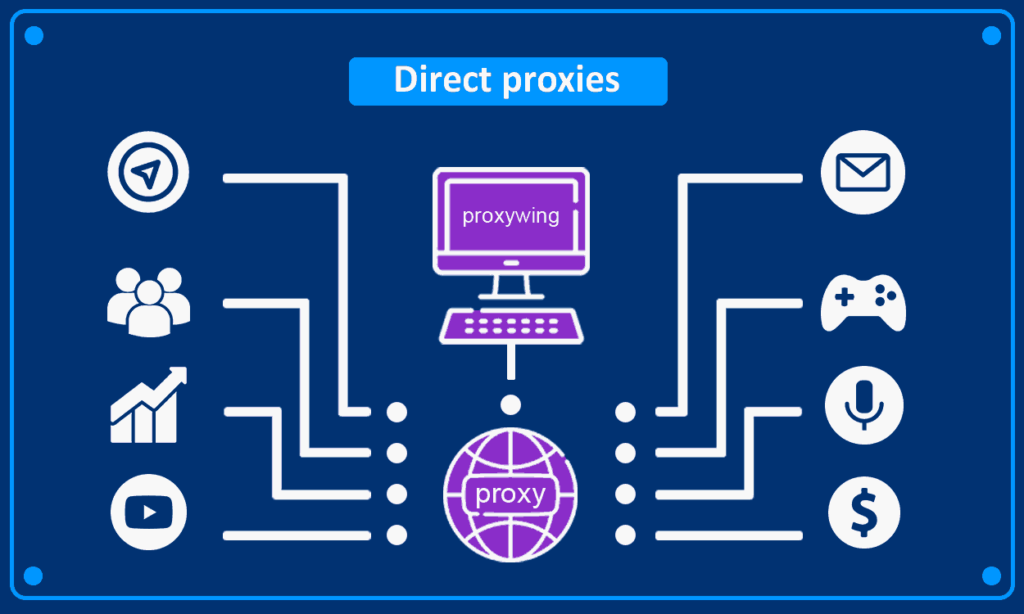
It acts on behalf of the client receiving requests from users and routing them into the open internet world. The main task is to provide anonymity, filtering of content, and blocking evasion. For instance, it hides your IP which allows users in one country with access to content, i.e., TV shows unavailable in that country.
Reverse Proxy
On the other hand, a reverse proxy is an intermediary server, which receives clients requests trying to access the domains of the site and then forwards them to the backend. Its primary functions include load balancing, SSL encryption, caching content, and blocking users from seeing server information. Reverse proxies prevent users from viewing the backend web servers of a website, thus improving security.
Why Use a Reverse Proxy Rather Than a Forward Proxy?
Reverse proxy is used mostly for web application and web site security and performance enhancement. It acts as a gateway between clients and back-end servers where the original server IPs are hidden to prevent any threat from reaching them while traffic is handled and SSL is encrypted and decrypted. Reverse proxies enhance the performance and availability of a site by caching responses and optimizing traffic. A forward proxy won’t work here, purely because its typical use is to hide the client’s IP address.
How a Reverse Proxy Works
A reverse proxy works by doing three significant things:
- Request handling: A user asks for something—maybe to go to a specific webpage or use an application. Instead of going straight to the backend server, however, this request is sent to the reverse proxy server.
- Processing: The reverse proxy server considers this request and determines what backend server would be best placed to respond. It can modify the request sometimes, adding things such as authentication or encryption information, before forwarding it to the destination server.
- Response Delivery: Once the request is handled by the backend server, it receives the response from the backend server and forwards it to the user without exposing the details of the backend server.
In essence, a reverse proxy serves as the go-between between users and backend servers and offers efficiency, security, and scalability.
Benefits of Having a Reverse Proxy
- Improved Security
It can perform several important security roles, including:
- Hides Backend Servers: It hides the backend servers, effectively obscuring their IP addresses and rendering them harder to target for attackers.
- DDoS Protection: This advanced system is capable of detecting and repelling Distributed Denial of Service (DDoS) attacks by eliminating suspicious traffic even before it hits the servers. This protects web applications or sites online even when the attackers attempt to overload it with a torrent of fake traffic.
- Web Application Firewall (WAF): The majority of reverse proxies have WAFs integrated, which can prove to be beneficial for capturing malicious connection requests and protecting against attacks like SQL injection and cross-site scripting (XSS).
- SSL Termination: With the processing of SSL encryption, it removes this computationally intensive process from backend servers with assurance of safe, encrypted traffic, addressing security concerns without compromising performance.
- Load Balancing and Traffic Management
It effectively divides incoming traffic across multiple servers to avoid overwhelming one server and providing seamless performance. It also supports better failover management by routing traffic to operational servers in case one goes down, thus offering high availability. It also facilitates scalability by adding or subtracting backend servers without affecting users or their requests.
- Content Caching and Performance Boost
Reverse proxies improve performance through caching of frequently accessed content like web pages and images so as to react more rapidly and cut down the load on the server. Placing cached content in proximity to users eliminates latency tremendously, thus decreasing time to display content to users since the page loads faster. This smart use of caching further optimizes bandwidth because certain content can be delivered directly from the cache without constantly fetching it.
- Data Privacy and Anonymity
They ensure privacy and security by hiding the identity of the backend servers and thus preventing immediate attacks. Reverse proxies also make compliance easier by routing traffic and hiding sensitive data from being exposed to end users, who may happen to be intruders at worst.
Use Cases of a Reverse Proxy
Below are some of the four typical use cases of reverse proxies:
- Securing Unmanaged Devices
End-users use unmanaged or personal devices to access company resources, thus bringing security threats. Security can be enforced by filtering and handling requests from these unmanaged devices before they access internal systems through a reverse proxy. For instance, it can be configured to permit secure access to sensitive applications only for those devices that meet some security requirements, for instance, being on the latest operating system.
- Data Protection for Businesses
Today, companies consider it necessary to implement stringent measures in protecting sensitive data in transit and at rest. Reverse proxies have made it possible to introduce an added layer of protection, adding encryption to the communications and hiding backend servers IP addresses from possible exposure. For instance, an enterprise business can implement a reverse proxy to protect client transactional data, with the option to manage encryption and server detail hiding.
- Threat Detection and Prevention
Security is purely protection against and prevention of malicious traffic to backend servers. Using a barrier, the reverse proxy screens incoming requests (http headers), looking for any indication of malicious behavior while filtering out known attacks such as DDoS, malware, and unauthorized requests.
- Successful Load Balancing
Companies need to manage high traffic levels effectively and maintain servers running even during peak usage periods. They allow distributing incoming requests between a cluster of servers so that one server is not overburdened. They can also be set up to divide traffic according to the type of request to allow accessing resources it needs. For example, Netflix and other streaming platforms use reverse proxies to distribute traffic across various data centers in order to deliver continuous video streaming to millions of users globally.
Challenges Faced by Reverse Proxies
Although reverse proxies offer a number of advantages, they also present some challenges that need to be overcome by organizations, ensuring smooth functioning. Here is a detailed analysis:
1. Complications in Configuration
Setting up is sophisticated coordination to work with backend servers, load balancers, and security layers. Misconfiguration leads to downtime or lost request routing. Integration with other systems (e.g., SSL certificates or DNS) can be cumbersome. There is technical knowledge needed for these tasks, and there are not many companies that possess it. Outside people must be hired, and that is costly for small brands.
Solution:
- Use software with simple-to-use UIs such as Nginx and with quality documentation.
- Automate the configuration via scripts or configuration management tools such as Ansible.
- Test and validate configurations regularly in a staging environment prior to deployment.
2. Latency Issues and Solutions
Usage of reverse proxies adds an additional step in the network, which may lead to a delay in responses. For instance, inefficient load balancing or caching can be a reason for latency. Physical location between the proxy and the users can also create latency, affecting the end-user experience ultimately.
Solution:
- Use of content caching to eliminate backend server calls and latency
- Leverage CDN (Content Delivery Networks) integration to provide cached content in proximity to users reducing latency. This makes the webpage load faster.
- Dedicated proxy hardware and high-performance software (e.g., Envoy, Traefik).
3. Security Misconfigurations
A poorly configured reverse proxy can leave servers exposed rather than secure them. For example, insecurely controlled access controls can provide unauthorized access and unpatched reverse proxy software can provide an attack surface.
Solutions:
- Keep its software updated to plug any loopholes.
- Implement security controls such as Web Application Firewalls (WAF) and robust access controls.
- Conduct regular audits of configurations to avoid exposing unintentionally.
4. Probability of Single Point of Failure
If a reverse proxy crashes, all the backend servers it’s serving might be out of commission. Lack of redundancy (using a single server) can cause downtime, and overwhelmed reverse proxies can cause crashes, making them unavailable to clients.
To avoid these risks, do the following:
- Use a high-availability (HA) setup with failover capabilities
- Use load balancing between the proxies themselves.
- Use performance monitoring tools like Prometheus or Grafana to detect problems and fix them in real time.
FAQs
How does a reverse proxy protect against DDoS attacks?
A reverse proxy is a very powerful shield against DDoS attacks, eliminating malicious traffic before it even reaches the backend servers. It effectively rate-limits requests and shields the servers from getting overloaded by identifying and blocking suspicious traffic patterns, keeping them running twenty-four hours a day.
Can a reverse proxy load balance to more than one backend server?
Yes, it can indeed load balance to more than one backend server. It is normally used for load balancing, where the proxy divides the requests among servers for better performance without having any one of them overwhelmed. Additionally, there is the option of configuring them to balance the traffic based on responsiveness as well as the availability of any server at a given time.
What’s the difference between a reverse proxy and a VPN, then?
A reverse proxy offers server protection by shielding incoming client requests and passing them along securely to the backend servers. A VPN safeguards users by encrypting their internet traffic and hiding their IP addresses, thereby guarding confidentiality while they browse the web. These two tools are designed with the idea of serving different security functions in that one guards servers while the other prioritizes user confidentiality, allowing a secured connection.