What Is a Proxy Firewall and How Does It Work?
A proxy firewall is an added layer of security that inspects data in application layers. It filters network traffic before providing it to internal devices. This helps protect from most web threats.
Article’s Key Takeways
- A proxy firewall strengthens network defense by inspecting traffic at the application layer, uncovering hidden malware and enforcing stricter security controls than traditional firewalls.
- It works as an intermediary between internal machines and the internet, masking IP addresses, applying content filters, and caching frequently accessed resources to improve both security and performance.
- Organizations often rely on proxy firewalls to standardize access policies, safeguard sensitive data, and regulate traffic across departments or regional offices. While the benefits include deep threat detection, user anonymity, and centralized logging, drawbacks such as higher costs, slower performance, and administrative complexity remain important considerations.
- Overall, proxy firewalls represent a robust yet resource-intensive solution for businesses facing growing cybersecurity challenges.
Traditional packet filters might simply cache certain data packets. A proxy firewall, on the other hand, examines full packets. It detects hidden malware and suspicious code.
Many companies use a proxy firewall to avoid web exposure and improve security. To learn how a proxy firewall works, how it compares with traditional firewalls, and how you might adapt one for your networks, read on.
What Are Proxy Firewalls?

Proxy firewalls are among the firewalls that test network traffic at deeper application layers. Unlike other methods that rely on IP addresses and internet protocols or simpler packet filters, they review the entire text of all data packets. Proxy firewalls offer firewall functionality beyond simple packet-filtering firewalls.
They often run on specialized servers within an organization’s security systems. In this architecture, specialized servers act as intermediaries, processing requests to ensure compliance with security policies before forwarding them to internal resources. Many companies also deploy a proxy server firewall or even more firewall proxy servers. Each is set in front of internal networks to handle general usage of the internet.
This setup allows proxy firewalls to intercept user requests to web applications. It checks security rules before forwarding. Because of that, your proxy firewall can catch threats that less sophisticated screening will not. It offers an ensured secured connection point for your local machines as well as hiding your internal IP addresses. It uses deep scanning, filters, and web caching.
Key Features of Proxy Firewalls:
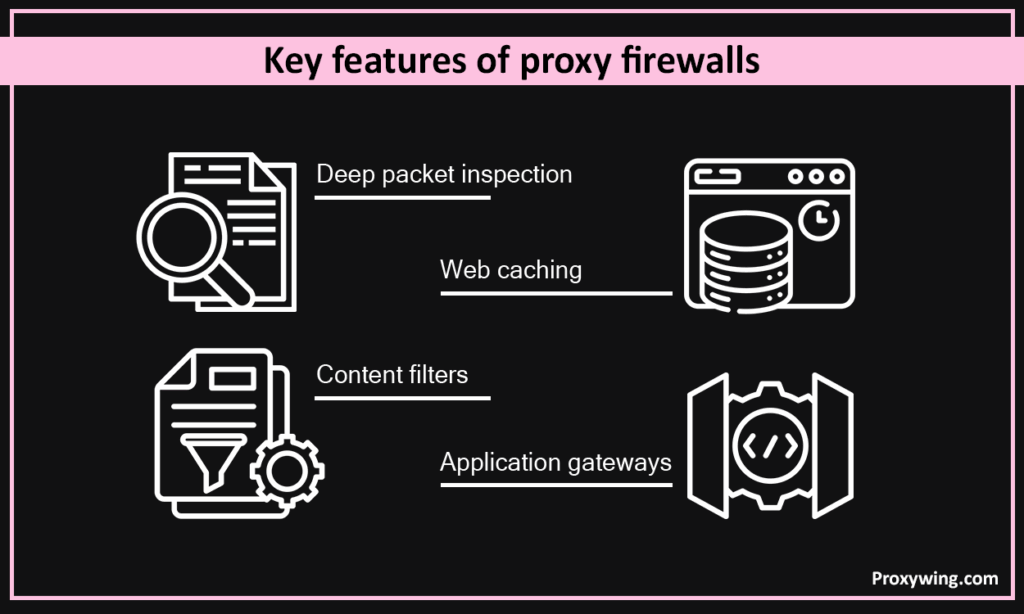
- Deep packet inspection. The proxy firewall examines embedded code or malware in packets at the application layer.
- Content filters. It prevents accessing suspicious webpages or illegal file downloads, controls access precisely, providing you with one more layer of security.
- Web caching. Many installations will cache frequently used webpages to speed connection times and cut down bandwidth use.
- Application gateways. The proxy firewall typically works with HTTP or FTP-based application protocols, providing services that have built-in security controls.
By providing those features, proxy firewalls help protect networks from advanced attacks and provide logs to audit in the future. They also add another layer of protection that organizations with greater security demands require.
How Do Proxy Firewalls Work?
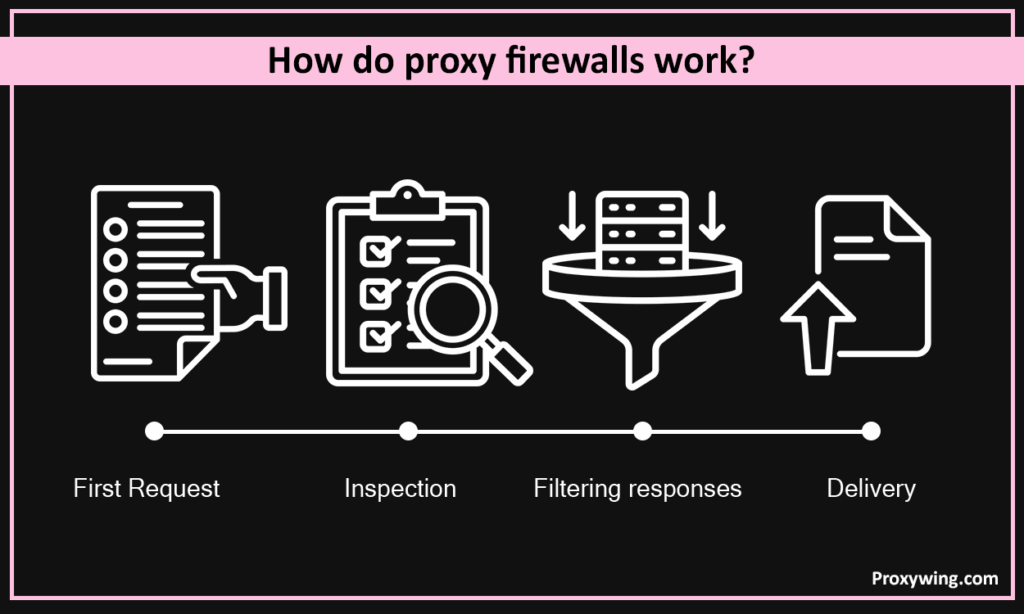
When local machines send requests to use a web application or even an online service, these requests are first sent to the proxy firewall. The firewall inspects packets at the application layers. It creates a secure connection only if the request is safe. This happens only if the requests comply with security policies. The interior machine is not directly connected with the outside internet.
- First Request. The client directs its network traffic to the proxy to access a public internet web service.
- Inspection. The proxy firewall also inspects packets for suspicious or malicious data.
- Decision. It accepts or rejects the packet whether it is secure or violates rules.
- Filtering responses. The remote server’s response also passes through the proxy firewall for an additional scan.
- Delivery. The final content is only presented to the consumer after ensuring that it is clean.
Inbound and outbound connections and traffics are analyzed by proxy firewalls to prevent hidden threats from coming in through your network.
How Are Proxy Firewalls Used?

Most companies use proxy firewalls to regulate their internal network traffic and access controls. One proxy would serve all an employee’s requests with tight filters. Others use various proxies for different departments or purposes. A research laboratory, for instance, might prefer full content scanning to protect confidential data. A large retailer may use them to scan viruses or block unauthorized websites.
Others also install a firewall proxy server in every regional office. This lets them keep security rules the same everywhere. This reduces bandwidth expenses as well as accelerates day-to-day operations. Regardless of the method used, the final goal remains identical: a proxy firewall protects precious internal machines from direct connections from the outside.
Proxy Firewall vs. Traditional Firewall: Comparison
Here is a concise comparison chart of proxy firewalls versus traditional firewalls. Look at how both products target security, performance, cost, and the optimal setting in which to use them.
| Security Method | Impact on Performance | Cost | Use Case |
| Application layer filter, conceals true IP addresses. | Can slow down traffic if not optimized; performs deep inspection of all data packets. | Typically higher due to advanced software/hardware. | Ideal for highly secure environments like finance, where detailed scanning is critical. |
| Traditional firewalls use basic IP rules and packet filters. | Faster overall; does not inspect full content at the application level. | Generally lower; off-the-shelf hardware often works. | Best for standard networks where speed matters more than deep inspection. |
The proxy firewall will more likely detect more complex attacks but is more resource-intensive. The default method is faster and simpler but misses more detailed content inspection.
Examples of How Proxy Firewalls Operate
Imagine a lawyer’s office maintaining confidential client documents. It scans or filters legal briefs downloaded for bad code. When users repeatedly request access to the same huge file, it caches files for faster access.
Take an online shopping site, for instance. It might rely on proxy firewalls to capture online transactions or buyer information. It blocks access to suspicious pay URLs in their entirety.
Caching web pages or graphics also accelerates routine operations. Both are examples of how these firewalls combine security with performance gains. These firewall deployments illustrate different firewall use cases in real-world scenarios. This helps optimize overall network traffic.
Proxy Firewall Benefits
Below are some of the reasons to use a proxy firewall:
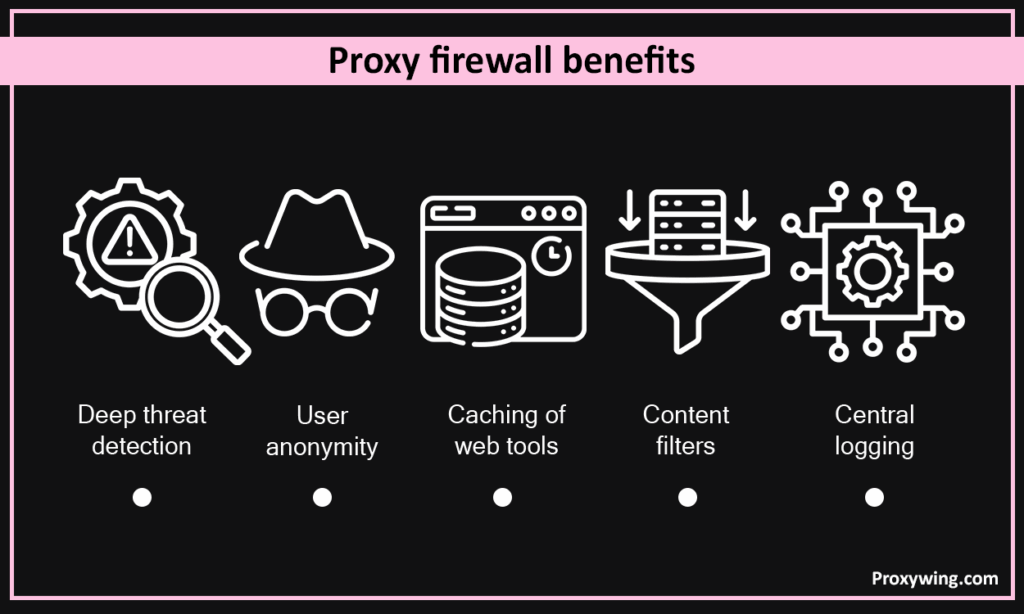
- Deep Threat Detection. Detects deep-level threats by scanning full application data.
- User Anonymity. Outsiders see only the firewall’s address. Your devices stay anonymous.
- Content filters. The administrator can select which websites or file types continue to be blocked, controlling web connections with precision.
- Caching of web tools. Caching saves time and bandwidth.
- Central Logging. A proxy firewall logs all network activity, which simplifies investigations in the event of a breach.
- Layered Firewall Protection. Works with existing network firewalls for a layered defense.
These benefits make proxy firewalls perfect for companies handling confidential data or organizations that must remain compliant. The firewall enforces standardized internet usage policies throughout the entire environment.
Proxy Firewalls Drawbacks

In addition to its benefits, a proxy firewall also possesses some potential shortcomings:
- Performance Bottlenecks. Parsing each data packet is CPU-heavy. With weak hardware, networks slow down.
- Increased Cost. Advanced scanning engines with tailor-made configurations are more costly.
- Incompatible Protocols. Legacy or traditional application protocols can be incompatible with rigorous inspection methods.
- False blocks. Overreaching content filters will block legitimate requests, imposing more administrative overhead.
- Complex Firewall Management. Integrating proxy firewalls with other firewalls increases administrative tasks
Business organizations must weigh those negatives against the greater security provided by a proxy firewall. The extra effort is worth it for stronger network security.
How Proxy Firewalls Handle Requests from the Internal Network
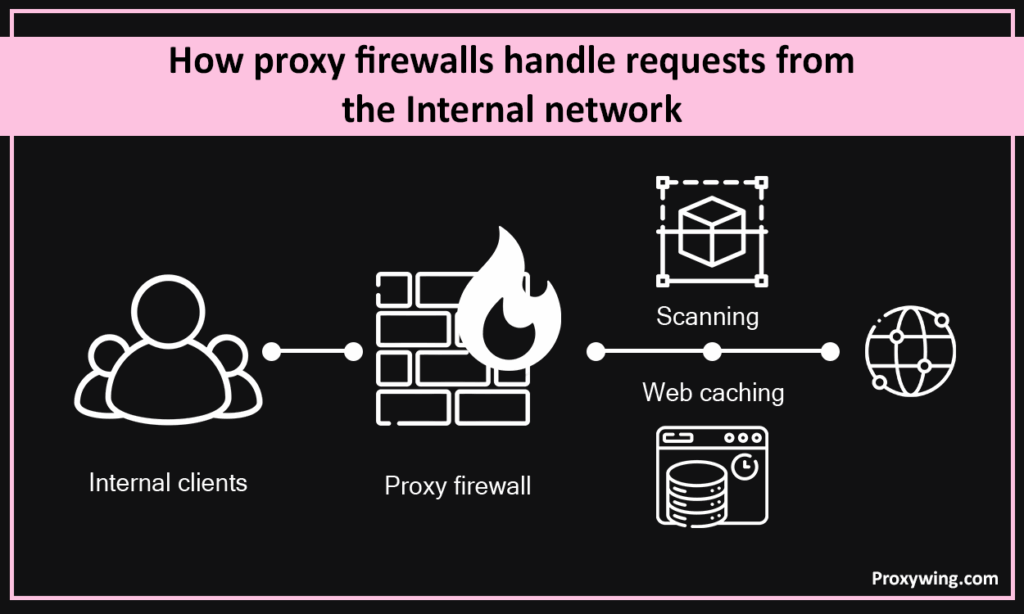
Your traffic from computers is filtered where you have implemented a proxy firewall. Your internal clients only connect to this proxy, which scans content based upon predefined scanning, access controls, and antivirus inspection. If there’s clean data, then it is allowed to be routed through.
This setup also supports caching web content. Proxy firewalls store frequently accessed web pages or documents, which reduces repeated bandwidth usage. That fosters quicker connections to end-users.
Most modern ones also handle SSL/TLS streams temporarily, scanning them for hidden threats before re-encrypting for final delivery. This step builds safer internet connections without ignoring malware, which might otherwise slip by.
Conclusion
A proxy firewall offers robust security through detailed examination of layers of applications to stop malicious content. It diverges from mere filtering since it also includes supplementary scanning, IP masking, content filters, and caching. It may be more expensive to purchase and fully automate Still, it’s essential in many companies. It helps protect networks and keeps internet use safe day to day.
A proxy firewall is a smart solution to rising cyber threats. It filters, logs, and protects your network from malicious traffic. Even small setups benefit and reduce misuse. It protects all critical data and services daily.
FAQ
Can a proxy firewall protect against malware and viruses?
Yes. By screening out application-layer data packets, a proxy firewall traps malicious code and prevents harmful files from entering, applying strict filtering rules to spare networks from most virus or malware attacks.
Is VPN a proxy firewall?
Not at all. A VPN secures users’ connections for safe remote links, while a proxy firewall monitors and sifts through traffic content at the application layers, hides internal IP addresses, and blocks hidden threats.
Can a proxy firewall block specific websites or applications?
Yes, proxy firewalls can block applications or sites. By strict content filters and access controls, they halt unwanted requests, allowing only authorized web services through the secure network infrastructure.