Anonymous Proxy vs VPN: Which One Fits Your Tasks?
When browsing the internet, one of the most effective ways to keep your internet activity private is by using a VPN or an anonymous proxy. Although both tools can be used to enhance online privacy, they offer different capabilities and have pros and cons that you should understand before choosing which one suits your needs.
In this anonymous proxy vs. VPN guide, we will dive into the main differences and the best use cases for each. By the end of this guide, you will know whether you need an anonymous proxy server or a VPN. So, without wasting any more of your time, let’s jump right in!
Anonymous Proxy vs VPN: A Complete Comparable Table
| Criteria | Anonymous Proxy | VPN |
| Encryption | None (typically) | High-level (AES-256) |
| Privacy | Hides IP from website only | Hides IP from website & ISP |
| Coverage | Single app/browser | Entire device |
| Block Risk | Generally low (Depends on proxy server type) | Moderate (cycles IPs) |
| Speed | Faster browsing speeds (no encryption lag) | Slower due encryption overhead |
| IP Control | High (easy IP rotation) | Moderate (server-based) |
| Setup | Manual in device or browser settings | Simple (app-based) |
| Best Use Case | Scraping & targeted tasks | General security & streaming |
What an Anonymous Proxy Is
An anonymous proxy is an intermediary server that hides your device network address from websites and online services you access. When using it, your traffic is routed through an IP address of a proxy server before it is sent to the target online service you intend to access. In the process, your device’s IP address is replaced with the proxy’s IP.
Unlike a transparent proxy, which shares your real network address, an anonymous proxy keeps your device’s IP address hidden but often still identifies itself as a proxy server. Elite (high-anonymity) proxies go a step further by hiding both your network address and the fact that a proxy is being used at all. Using elite proxies is usually necessary if you need to access websites that restrict proxy server usage.
What “anonymous” means in proxy terms
As far as proxies are concerned, it specifically refers to the masking of the HTTP_X_FORWARDED_FOR header. It is this header that usually carries your real device network address. Even though the network address is hidden, the proxy server may still send the HTTP_VIA header that tells the destination server that the request is coming through a middleman. If this header is sent, the target server will know that traffic is coming from a proxy server.
Typical scenarios where anonymous proxies are used
- Privacy-lite browsing: An anonymous proxy server allows anonymous browsing by hiding your IP address, which makes your connection more anonymous.
- Geo-testing: Developers can use them to test how their apps or websites perform in different countries.
- Web scraping: When web scraping, an anonymous proxy helps to automatically rotate IPs to avoid having many requests coming from the same address, which can often lead to IP blocks.
- Account management: Managing multiple social or business profiles. Proxies help prevent account bans by allocating each account a different IP when managing them on the same device.
- Ad verification: Businesses can check if ads are displayed correctly and securely in the different regions they target.
- Bypassing simple filters: Proxies can help bypass restrictions implemented by schools or office firewalls.
When using them, it is important to always comply with the website’s Terms of Service (ToS) and local data privacy laws.
How an Anonymous Proxy Works
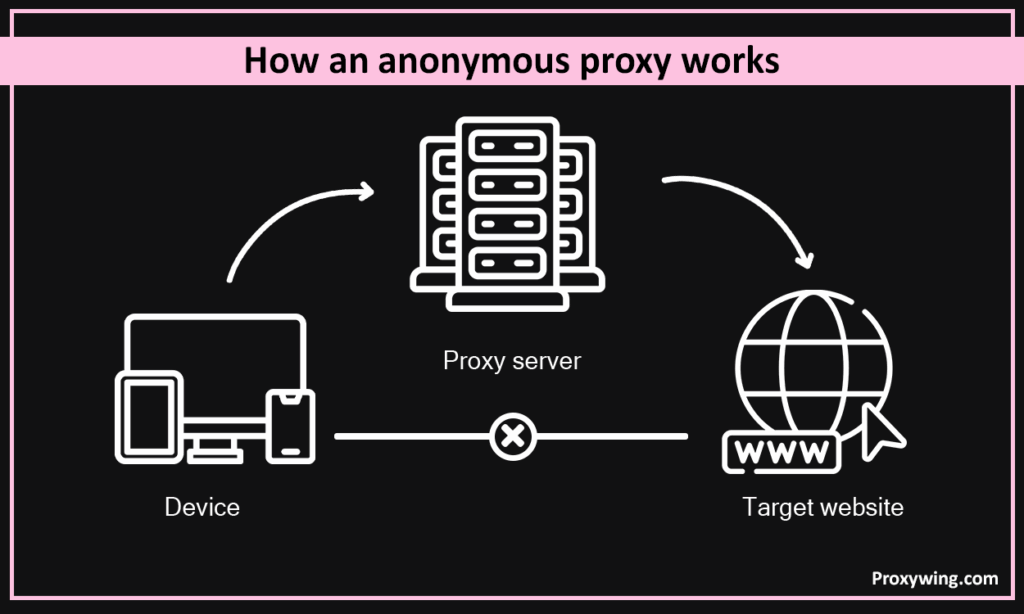
When using it, your traffic will travel following this path: Device → Proxy Server → Target Website. That means the anonymous proxy intercepts your request, strips your network address, and replaces it with its own. The website will see your traffic as though it is coming from the proxy’s IP address as the origin, ensuring more secure connections.
What a website can still see
Even though the anonymous proxy server masks your network address and location, some of your traffic details will still be exposed to the websites. Such details include:
- Browser Fingerprinting: Unique combinations of your browser settings, including screen resolution, OS, fonts, and more.
- Cookies: Tracking files stored on your device from previous visits to the website.
- Account Signals: If you log into a service like Google, the anonymous proxy is irrelevant since these sites already have your identity details.
- Behavioral Patterns: How fast you click or move your mouse.
Levels of Proxy Anonymity
Proxy anonymity includes three levels:
Transparent proxy
These are primarily used by organizations to filter content or web caching to improve performance. They offer no privacy at all since they pass your real network address in the headers.
Anonymous proxy
An anonymous proxy hides your real network address, but does not hide the fact that you are using a proxy by forwarding the HTTP_VIA header. If the website restricts proxy server usage, your connection can be interfered with.
Elite (high-anonymity) proxy
An elite proxy provides the highest level of proxy security since it hides your network address and does not send any headers that identify the server as a proxy. To the website, the connection looks like a standard residential user.
What a VPN Is
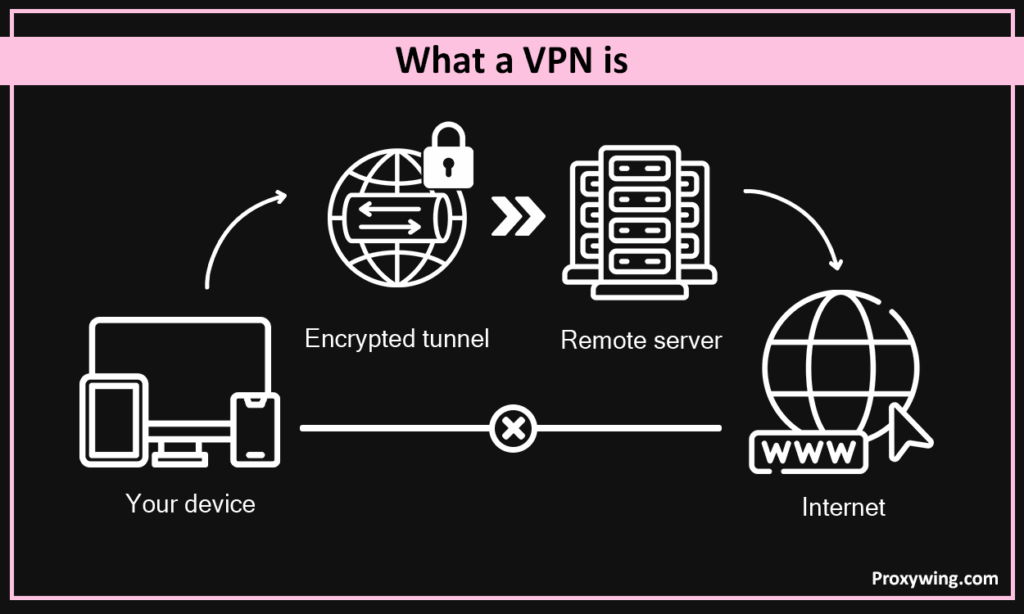
It is a secure, encrypted tunnel between your device and a remote server. When using a VPN, all your traffic is sent using this secure tunnel. Unlike a proxy, which usually works at the app level (like a browser), a VPN typically operates at the Operating System level. When it is turned on, all traffic leaving your device goes through encrypted tunnels unless you enable split tunneling.
How VPN tunneling works
Tunneling protects your data using three main steps:
- Data encryption: The VPN clients encrypt your data using modern encryption protocols before it leaves your device.
- Secure tunnel: It creates a secure tunnel. All the encrypted data leaving your device is sent via these secure tunnels.
- VPN server decrypts traffic: Finally, the server decrypts your data and sends it to the internet with a new network address. The response from the target server is sent following the same path.
Split tunneling (why it matters)
Split tunneling gives users the choice to determine which traffic goes through the VPN and which use the open internet. This is useful for accessing content on websites that restrict VPN usage, while simultaneously browsing the rest of the web securely. However, it is crucial to carefully configure split tunneling and make sure all the necessary traffic uses a secure tunnel to avoid unintended data leaks if it is accidentally not encrypted.
Types of VPNs
Corporate VPN
It is primarily designed to enable remote workers to access a company’s internal network (intranet). These virtual private networks provide admins the flexibility to manage who sees sensitive company files and who doesn’t. They are not specifically meant to provide internet anonymity.
Individual VPN
This is designed to enhance personal privacy by encrypting their traffic before sending it over to the internet. These services focus on masking your web browsing activity from internet service providers, protecting data when using public networks like airport WiFi. It also helps with bypassing geographical content restrictions on streaming platforms.
Proxy vs VPN: The Key Differences
The primary difference between the two lies in scope and encryption. Here is a summary of the differences in the table below:
| Feature | Anonymous Proxy | VPN |
| Scope | App-level (e.g., Browser) | OS-level (Entire device) |
| Encryption | None (unless HTTPS/SOCKS5) | High-level (AES-256) |
| Performance | Faster connections (less overhead) | Slower (encryption lag) |
| Manageability | Highly granular | “Set and forget” |
Let’s explore all the differences in more detail:
Security (encryption and threat surface)
VPNs automatically encrypt all data leaving your device, making it invisible to anyone on the network, including ISPs. Most proxies do not encrypt your data. That means if you use an anonymous proxy on an unsecured network, an attacker could still see your traffic content (when accessing non-HTTPs websites) even if your network address is hidden.
Privacy (what gets hidden)
Proxies hide your network address and location. On the other hand, virtual private networks offer “full-tunnel” routing, hiding your network address and most of your browsing details. However, both tools will not hide your identity if you are logged into an account or have unique browser fingerprints.
Speed and latency
Proxies generally offer higher connection speeds because they don’t include the encryption step. This makes them a better option for high-bandwidth tasks like web scraping. VPNs add overhead due to the encryption/decryption process, which can slightly affect the performance.
Coverage: single app vs whole device
An anonymous proxy in some cases has to be configured inside each specific app (e.g., Chrome, Telegram). A VPN on the other hand automatically covers the entire device, unless you specifically exclude apps using split tunneling.
Detection and blocking risk
VPNs use well-known datacenter IP ranges that most firewalls often block. They also usually have a few network addresses generated by the virtual private networks providers. Traffic from proxies, especially residential proxy services is harder to detect because it is similar to the standard home internet connections.
Proxy Types
Here are some of the common proxy classifications
By direction: Forward proxy
A forward proxy server is the standard type used by clients. It sits in front of the user and forwards their web requests to the target websites, after masking their network address and location.
By visibility: Transparent vs anonymous vs high anonymity
- Transparent Proxy: Identifies itself as a proxy and also reveals your real network address.
- Anonymous Proxy: Only hides your device network address, but still identifies itself as a proxy.
- High Anonymity (Elite) Proxy: Provides anonymity by hiding your network address and does not reveal its proxy status.
By IP source: Datacenter vs Residential vs ISP
- Datacenter: These use IPs from datacenters. Traffic is routed through datacenter IPs before it forwards requests to the target website. Datacenter proxies are the fastest and cheapest, but also the easiest to detect and block.
- Residential: IPs sourced from real home devices, making them highly trusted. However, they are also the most expensive.
- ISP: proxy servers using IP addresses provided by internet service providers. They combine the high speed and stability of datacenter proxies with the anonymity and reliability of residential proxies.
By access model: Public, shared, dedicated
- Public: IPs are shared among several users. They are free and have a high risk of data theft.
- Shared: The IP address is used by multiple people. They are cheaper, but other users could get the IP you are using banned, causing frequent connection drops on certain websites.
- Dedicated: You are the only user of the IP.
By protocol: HTTP(S) / SSL proxy vs SOCKS
- HTTP Proxy: These are designed for only web traffic. They can interpret and filter web pages.
- SOCKS5 Proxy: These are more flexible and can handle any traffic, including gaming, torrents, VOIP, or file sharing at a lower level.
Anonymous Proxy vs VPN: Which One Should You Use?
- Choose a Proxy if: You need high-speed, targeted routing for specific tasks such as web scraping, managing multiple social profiles, or bypassing a single site’s geo-block.
- Choose VPNs if: You need “always-on” security and privacy for your whole device. They are the best choice when working on public Wi-Fi, streaming movies from abroad, or hiding browsing activities from your ISP.
How to Set Up and Use an Anonymous Proxy
After purchase, the provider will give you all the proxy details, including IP address (hostname) and port. They may also provide authentication details if necessary. You should then add these proxy details in your device network settings.
Depending on your operating system, you need to find the proxy option in your network settings and add these settings. Remember, a proxy only works with one network at a time. Connecting to a different one will require setting it up for that network as well. If you are using web browsers like Firefox or Tor browser, you can integrate the proxy details directly into the browser settings.
Troubleshooting
Here is how to fix some of the common proxy errors:
- Auth Errors: Double-check your credentials or whitelist (make sure you provide the correct IP address).
- Timeouts: The proxy server may be overloaded. Try another IP if you have the option.
- Leaks: Use a site like browserleaks.com to ensure your real IP isn’t “leaking” through WebRTC.
Safety Tips
- Always use HTTPS: Since proxies often don’t encrypt traffic, ensure the website you visit is encrypted with valid SSL certificates.
- Avoid “Free” Proxies: These usually sell user’s private data to generate revenue.
- Audit Permissions: Only give proxy access to the apps that absolutely need it.
Wrap-up
The choice between proxies and virtual private networks will largely go down to what you intend to do on the internet and your priorities. Go for virtual private networks if you want a simple, one-click solution for broad security of your device or accessing blocked contents in your country. Anonymous or elite proxies are the best choice if you need precise control over your IP reputation and want to have the fastest internet speeds for tasks like web scraping or online gaming.
FAQs
Do you need a proxy if you have a VPN?
Usually, no. A VPN does everything a proxy does and more. However, using a proxy is necessary if you need more control over the IP addresses you use. Proxies provide extra capabilities like IP rotation and more precise geo-targeting that VPNs don’t offer.
Is an anonymous proxy the same as incognito mode?
No. Incognito mode only prevents your browser from saving history and cookies. Unlike proxies, it does not hide your IP address from the websites you visit or your ISP.
Can a VPN hide you from websites completely?
It hides your IP address and encrypts your internet traffic, masking both your physical location and the specific content of your online activity from third parties. However, if you are logged in to the website, you won’t be anonymous since you already provided your identity details.